Enhanced Open Beacon
Enhanced Open の Beacon フレームをキャプチャしてみました。
opmode-transition が有効 (default) な SSID 「bin4-enhanced-open-trans」と opmode-transition が無効な SSID 「bin4-enhanced-open」、比較として Open モードの SSID 「bin4-open」を設定しました。
- show ap bss-table コマンド
AP505# show ap bss-table Aruba AP BSS Table ------------------ bss ess port ip phy type ch/EIRP/max-EIRP cur-cl ap name in-t(s) tot-t flags --- --- ---- -- --- ---- ---------------- ------ ------- ------- ----- ----- b8:3a:5a:8b:36:d0 bin4-enhanced-open ?/? 192.168.215.13 a-HE ap 44/20.0/23.0 0 AP505 0 10m:28s WET b8:3a:5a:8b:36:d1 bin4-enhanced-open-trans ?/? 192.168.215.13 a-HE ap 44/20.0/23.0 0 AP505 0 10m:28s oT b8:3a:5a:8b:36:d2 _owetm_bin4-enhanced-1803478119 ?/? 192.168.215.13 a-HE ap 44/20.0/23.0 0 AP505 0 10m:28s WOT b8:3a:5a:8b:36:d3 bin4-open ?/? 192.168.215.13 a-HE ap 44/20.0/23.0 0 AP505 0 10m:28s T Channel followed by "*" indicates channel selected due to unsupported configured channel. "Spectrum" followed by "^" indicates Local Spectrum Override in effect. Num APs:5 Num Associations:0 Flags: K = 802.11K Enabled; W = 802.11W Enabled; r = 802.11r Enabled; 3 = WPA3 BSS; O = Enhanced-open BSS with transition mode; o = Enhanced-open transition mode open BSS; M = WPA3-SAE mixed mode BSS; E = Enhanced-open BSS without transition mode; m = Agile Multiband (MBO) BSS; c = MBO Cellular Data Capable BSS; I = Imminent VAP Down; T = Individual TWT Enabled; t = Broadcast TWT Enabled; d = Deferred Delete Pending; a = Airslice policy; A = Airslice app monitoring; D = VLAN Discovered; AP505#
- bin4-enhanced-open-trans (opmode-transitionが有効) の Beacon フレーム
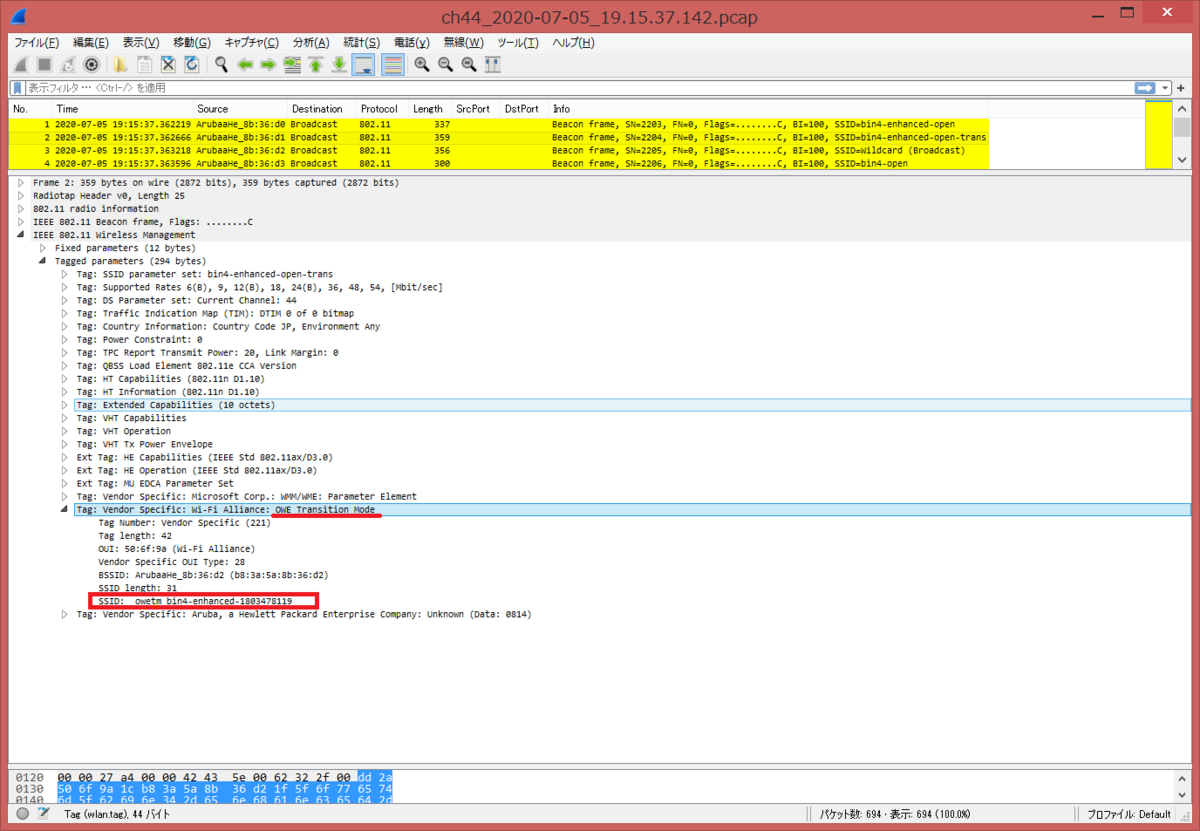
OWE Transition Mode タグに SSID: _owetm_bin4-enhanced-1803478119 が埋め込まれていることが分かる。RSN Information タグがなく、Open モードであることがわかる。

SSID が Wildcard (Hidden/Stealth) で、OWE Transition Mode タグに SSID: bin4-enhanced-open-trans が埋め込まれていることが分かる。また、RSN Information タグの AKM (Auth Key Management) に 00:0f:ac:12 (OWE) となっていることが確認できます。
- bin4-enhanced-open (opmode-transitionが無効) の Beacon フレーム

RSN Information タグの AKM (Auth Key Management) に 00:0f:ac:12 (OWE) となっていることが確認できます。また、OWE Transition Mode タグがないことが確認できます。
- bin4-open (Open モード) の Beacon フレーム

[English Version]
I captured Enhanced Open Beacon frames.
I set opmode-transition enabled SSID: bin4-enhanced-open-trans and disabled SSID: bin4-enhanced-open. For comparison. I also set bin4-open as Open mode.
- output of show ap bss-table
AP505# show ap bss-table Aruba AP BSS Table ------------------ bss ess port ip phy type ch/EIRP/max-EIRP cur-cl ap name in-t(s) tot-t flags --- --- ---- -- --- ---- ---------------- ------ ------- ------- ----- ----- b8:3a:5a:8b:36:d0 bin4-enhanced-open ?/? 192.168.215.13 a-HE ap 44/20.0/23.0 0 AP505 0 10m:28s WET b8:3a:5a:8b:36:d1 bin4-enhanced-open-trans ?/? 192.168.215.13 a-HE ap 44/20.0/23.0 0 AP505 0 10m:28s oT b8:3a:5a:8b:36:d2 _owetm_bin4-enhanced-1803478119 ?/? 192.168.215.13 a-HE ap 44/20.0/23.0 0 AP505 0 10m:28s WOT b8:3a:5a:8b:36:d3 bin4-open ?/? 192.168.215.13 a-HE ap 44/20.0/23.0 0 AP505 0 10m:28s T Channel followed by "*" indicates channel selected due to unsupported configured channel. "Spectrum" followed by "^" indicates Local Spectrum Override in effect. Num APs:5 Num Associations:0 Flags: K = 802.11K Enabled; W = 802.11W Enabled; r = 802.11r Enabled; 3 = WPA3 BSS; O = Enhanced-open BSS with transition mode; o = Enhanced-open transition mode open BSS; M = WPA3-SAE mixed mode BSS; E = Enhanced-open BSS without transition mode; m = Agile Multiband (MBO) BSS; c = MBO Cellular Data Capable BSS; I = Imminent VAP Down; T = Individual TWT Enabled; t = Broadcast TWT Enabled; d = Deferred Delete Pending; a = Airslice policy; A = Airslice app monitoring; D = VLAN Discovered; AP505#
- bin4-enhanced-open-trans (opmode-transition enabled) Beacon frame

In OWE Transition Mode Tag, there is SSID: _owetm_bin4-enhanced-1803478119. There is no RSN Information Tag, hence this means Open mode.

SSID is Wildcard (Hidden/Stealth) and In OWE Transition Mode Tag, there is SSID: bin4-enhanced-open-trans. In RSN Information tag, there is AKM (Auth Key Management) 00:0f:ac:12 (OWE).
- bin4-enhanced-open (opmode-transition disabled) Beacon frame

In RSN Information tag, there is AKM (Auth Key Management) 00:0f:ac:12 (OWE). There is no OWE Transition Mode Tag.
- bin4-open (Open mode) Beacon frame

Open Enhanced setting on Aruba AP505/Instant OS 8.7.0.0
Aruba AP505/Instant OS 8.7.0.0 を用いた Open Enhanced 設定を紹介します。
- Basic 設定

従来の Open モードの場合は、Primary usage に Guest を選択するが、下記の User Guide を見る限り、デフォルトの Employee を選択するようです。
https://www.arubanetworks.com/techdocs/Instant_87_WebHelp/Content/instant-ug/authentication/enhanced-open.htm
- VLAN 設定

- Security 設定

Security Level に Open を選択し、Enhanced Open が有効になっていることを確認する。
- Access 設定
AP505# show running-config wlan access-rule bin4-enhanced-open-trans index 3 rule any any match any any any permit wlan ssid-profile bin4-enhanced-open-trans enable index 1 type employee essid bin4-enhanced-open-trans opmode enhanced-open max-authentication-failures 0 rf-band all captive-portal disable dtim-period 1 broadcast-filter arp dmo-channel-utilization-threshold 90 local-probe-req-thresh 0 max-clients-threshold 64
また、Open Enhanced も opmode-transition コマンドがデフォルトで有効で、Open 用の SSID: bin4-enhanced-open-trans と Enhanced Open 用の SSID: _owetm_bin4-enhanced-1803478119 の2つの VAP が生成されます。そのため、VAP 数の制限が最大16個であれば、8個しか生成できないということになり、注意が必要です。
AP505# show ap bss-table Aruba AP BSS Table ------------------ bss ess port ip phy type ch/EIRP/max-EIRP cur-cl ap name in-t(s) tot-t flags --- --- ---- -- --- ---- ---------------- ------ ------- ------- ----- ----- b8:3a:5a:8b:36:d0 bin4-enhanced-open-trans ?/? 192.168.215.13 a-HE ap 140/18.0/29.7 0 AP505 0 2m:9s oT b8:3a:5a:8b:36:d1 _owetm_bin4-enhanced-1803478119 ?/? 192.168.215.13 a-HE ap 140/18.0/29.7 0 AP505 0 2m:8s WOT b8:3a:5a:8b:36:c0 bin4-enhanced-open-trans ?/? 192.168.215.13 g-HE ap 11/9.0/28.0 0 AP505 0 2m:9s oT b8:3a:5a:8b:36:c1 _owetm_bin4-enhanced-1803478119 ?/? 192.168.215.13 g-HE ap 11/9.0/28.0 0 AP505 0 2m:8s WOT Channel followed by "*" indicates channel selected due to unsupported configured channel. "Spectrum" followed by "^" indicates Local Spectrum Override in effect. Num APs:4 Num Associations:1 Flags: K = 802.11K Enabled; W = 802.11W Enabled; r = 802.11r Enabled; 3 = WPA3 BSS; O = Enhanced-open BSS with transition mode; o = Enhanced-open transition mode open BSS; M = WPA3-SAE mixed mode BSS; E = Enhanced-open BSS without transition mode; m = Agile Multiband (MBO) BSS; c = MBO Cellular Data Capable BSS; I = Imminent VAP Down; T = Individual TWT Enabled; t = Broadcast TWT Enabled; d = Deferred Delete Pending; a = Airslice policy; A = Airslice app monitoring; D = VLAN Discovered; AP505#
[English Version]
I introduce Open Enhanced configuration using Aruba AP505/Instant OS 8.7.0.0.
- Basic configuration

We usually select Guest as Primary usage, but for enhanced open, we need to select Employee with reference to User Guide.
https://www.arubanetworks.com/techdocs/Instant_87_WebHelp/Content/instant-ug/authentication/enhanced-open.htm
- VLAN configuration

- Security configuration

Select Open as Security Level and confirm Enhanced Open is enabled.
- Access configuration

AP505# show running-config wlan access-rule bin4-enhanced-open-trans index 3 rule any any match any any any permit wlan ssid-profile bin4-enhanced-open-trans enable index 1 type employee essid bin4-enhanced-open-trans opmode enhanced-open max-authentication-failures 0 rf-band all captive-portal disable dtim-period 1 broadcast-filter arp dmo-channel-utilization-threshold 90 local-probe-req-thresh 0 max-clients-threshold 64
opmode-transition is enabled by default. 2 VAPs are generated. SSID: bin4-enhanced-open-trans is for Open. SSID: _owetm_bin4-enhanced-1803478119 is for Enhanced open. Please note Enhanced open with opmode-transition consumes 2 VAPs, so if AP supports up to 16 VAPs, then we can create 8 Enhanced open ssids.
AP505# show ap bss-table Aruba AP BSS Table ------------------ bss ess port ip phy type ch/EIRP/max-EIRP cur-cl ap name in-t(s) tot-t flags --- --- ---- -- --- ---- ---------------- ------ ------- ------- ----- ----- b8:3a:5a:8b:36:d0 bin4-enhanced-open-trans ?/? 192.168.215.13 a-HE ap 140/18.0/29.7 0 AP505 0 2m:9s oT b8:3a:5a:8b:36:d1 _owetm_bin4-enhanced-1803478119 ?/? 192.168.215.13 a-HE ap 140/18.0/29.7 0 AP505 0 2m:8s WOT b8:3a:5a:8b:36:c0 bin4-enhanced-open-trans ?/? 192.168.215.13 g-HE ap 11/9.0/28.0 0 AP505 0 2m:9s oT b8:3a:5a:8b:36:c1 _owetm_bin4-enhanced-1803478119 ?/? 192.168.215.13 g-HE ap 11/9.0/28.0 0 AP505 0 2m:8s WOT Channel followed by "*" indicates channel selected due to unsupported configured channel. "Spectrum" followed by "^" indicates Local Spectrum Override in effect. Num APs:4 Num Associations:1 Flags: K = 802.11K Enabled; W = 802.11W Enabled; r = 802.11r Enabled; 3 = WPA3 BSS; O = Enhanced-open BSS with transition mode; o = Enhanced-open transition mode open BSS; M = WPA3-SAE mixed mode BSS; E = Enhanced-open BSS without transition mode; m = Agile Multiband (MBO) BSS; c = MBO Cellular Data Capable BSS; I = Imminent VAP Down; T = Individual TWT Enabled; t = Broadcast TWT Enabled; d = Deferred Delete Pending; a = Airslice policy; A = Airslice app monitoring; D = VLAN Discovered; AP505#
Open Enhanced / OWE (Opportunistic Wireless Encryption)
Open Enhanced は、文字通りオープンモードの拡張版で、OWE (Opportunistic Wireless Encryption)/RFC-8110 を用いて、パスワードを入力しないでも暗号キーを生成し、フレームを暗号化することが可能です。
Android 10 より、対応しているようです。
WPA3 and Wi-Fi Enhanced Open | Android Open Source Project
Apple 製品では未対応のようです。
https://discussions.apple.com/thread/251332529
[English Version]
"Open Enhanced" is literally enhanced open mode. This mode is based on OWE (Opportunistic Wireless Encryption)/RFC-8110. Customer does not need to input id/password but encryption key are generated by automatically, then frames are encrypted.
Android 10 supports Open Enhanced.
WPA3 and Wi-Fi Enhanced Open | Android Open Source Project
Apple devide does not support so far.
https://discussions.apple.com/thread/251332529
Failed to WPA3-Enterprise GCM256/CNSA
WPA3-Enterprise GCM256 および CNSA に iPhone SE/iOS13.5.1 を EAP-TLS で接続してみましたが、いずれも失敗しました。原因は不明です。EAP-PEAP もダメでした。以下は、EAP-TLS 使用時のログです。
- GCM256 接続時
AP が 4-way handshake の Key1 を再送しているログが見れますが、iPhone が key2 を返していないです。
AP505# show ap debug auth-trace-buf Auth Trace Buffer ----------------- Jul 4 15:52:05 wpa2-key1 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d1 - 117 Jul 4 15:52:07 wpa2-key1 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d1 - 117
- CNSA 接続時
wpa3-cnsa-key4 まで確認できますが、DHCP による IP アドレスが取得できていないです。
AP505# show ap debug auth-trace-buf
Auth Trace Buffer
-----------------
Jul 5 16:30:29 wpa3-cnsa-key1 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d2 - 125
Jul 5 16:30:29 wpa3-cnsa-key2 -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d2 - 147
Jul 5 16:30:29 wpa3-cnsa-key3 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d2 - 231
Jul 5 16:30:29 wpa3-cnsa-key4 -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d2 - 103
AP505# show clients debug
Client List
-----------
Name Host Name IP Address MAC Address OS ESSID Access Point Channel Type Role IPv6 Address Signal Speed (mbps) *Reauth Age *Reauth Interval *Reauth ESSID Auth Type *Authenticated DEL Age Vlan *ESSID *Private role info Accouting Session Name BSSID Idle Timeout csum *mcast groups *Acct Interval *Class Attribute *Dhcp-Opt Vlan *Dhcp-Opt role Intercept *Offline *FB Token *FB RxBytes *FB TxBytes *SLAAC IP Address *Link Local IP Address *DHCP Status *DHCP v6 Status
---- --------- ---------- ----------- -- ----- ------------ ------- ---- ---- ------------ ------ ------------ ----------- ---------------- ------------- --------- -------------- --- --- ---- ------ ------------------ ---------------------- ----- ------------ ---- ------------- -------------- ---------------- -------------- -------------- --------- -------- --------- ----------- ----------- ----------------- ---------------------- ------------ ---------------
0.0.0.0 84:ab:1a:11:d2:f6 NOFP bin4-wpa3-enterprise-cnsa AP505 108 a-HE bin4-wpa3-enterprise-cnsa -- 58(good) 8(poor) 18 0 bin4-wpa3-enterprise-cnsa 802.1x/TLS yes no 6 0(NONE) bin4-wpa3-enterprise-cnsa(EAP-TLS) 155(RADIUS-7fff) b8:3a:5a:8b:36:d2 1000 b4944a0d (0) 0 a3cbd30cf4d346e0beea50959a4419e8b90b0000000000005230303030303434392d30312d35663031383139350000000000000000000000 0,NONE ,,0-0 no no null null null 0.0.0.0 0.0.0.0 None None
AP505#
引き続き、調査します。
[English Version]
I tried to connect iPhone SE/iOS13.5.1 to Aruba AP505/Instant OS 8.7.0.0 WPA3-Enterprise GCM256 and CNSA with EAP-TLS, but could not. I am not sure what I missed. I also tried EAP-PEAP, but failed neither. Below is output using EAP-TLS
- Connecting to GCM256
We can AP sent 4-way handshake Key1, but STA did not send key2.
AP505# show ap debug auth-trace-buf Auth Trace Buffer ----------------- Jul 4 15:52:05 wpa2-key1 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d1 - 117 Jul 4 15:52:07 wpa2-key1 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d1 - 117
- Connecting to CNSA
We can see wpa3-cnsa-key4, but iPhone could not get IP address from the DHCP server.
AP505# show ap debug auth-trace-buf
Auth Trace Buffer
-----------------
Jul 5 16:30:29 wpa3-cnsa-key1 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d2 - 125
Jul 5 16:30:29 wpa3-cnsa-key2 -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d2 - 147
Jul 5 16:30:29 wpa3-cnsa-key3 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d2 - 231
Jul 5 16:30:29 wpa3-cnsa-key4 -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d2 - 103
AP505# show clients debug
Client List
-----------
Name Host Name IP Address MAC Address OS ESSID Access Point Channel Type Role IPv6 Address Signal Speed (mbps) *Reauth Age *Reauth Interval *Reauth ESSID Auth Type *Authenticated DEL Age Vlan *ESSID *Private role info Accouting Session Name BSSID Idle Timeout csum *mcast groups *Acct Interval *Class Attribute *Dhcp-Opt Vlan *Dhcp-Opt role Intercept *Offline *FB Token *FB RxBytes *FB TxBytes *SLAAC IP Address *Link Local IP Address *DHCP Status *DHCP v6 Status
---- --------- ---------- ----------- -- ----- ------------ ------- ---- ---- ------------ ------ ------------ ----------- ---------------- ------------- --------- -------------- --- --- ---- ------ ------------------ ---------------------- ----- ------------ ---- ------------- -------------- ---------------- -------------- -------------- --------- -------- --------- ----------- ----------- ----------------- ---------------------- ------------ ---------------
0.0.0.0 84:ab:1a:11:d2:f6 NOFP bin4-wpa3-enterprise-cnsa AP505 108 a-HE bin4-wpa3-enterprise-cnsa -- 58(good) 8(poor) 18 0 bin4-wpa3-enterprise-cnsa 802.1x/TLS yes no 6 0(NONE) bin4-wpa3-enterprise-cnsa(EAP-TLS) 155(RADIUS-7fff) b8:3a:5a:8b:36:d2 1000 b4944a0d (0) 0 a3cbd30cf4d346e0beea50959a4419e8b90b0000000000005230303030303434392d30312d35663031383139350000000000000000000000 0,NONE ,,0-0 no no null null null 0.0.0.0 0.0.0.0 None None
AP505#
I will try and update later.
WPA3-Enterprise CCM128
WPA3-Enterprise CCM128 (SSID: bin4-wpa3-enterprise-ccm128) に WPA3 対応の iPhone SE/iOS13.5.1 と WPA2 対応の Galaxy SC-04F/Android 6.0.1 を EAP-PEAP で接続してみました。WPA3-Enterprise CCM128 は、802.11w PMFC (Management Frame Protection Capable) が有効になっているが、WPA2-Enterprise とほぼ同等で、WPA2 対応端末も接続することが可能です。WPA3-Personal のように opmode-transition コマンドを有効にする必要はない。
AP505# show ap debug auth-trace-buf Auth Trace Buffer ----------------- Jul 3 18:40:19 station-up * 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - - wpa2 aes Jul 3 18:40:19 eap-id-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 1 5 Jul 3 18:40:19 eap-id-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 1 10 user1 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 85 215 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 85 - Jul 3 18:40:19 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 2 6 Jul 3 18:40:19 eap-nak -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 2 8 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 86 255 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 86 - Jul 3 18:40:19 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 3 6 Jul 3 18:40:19 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 3 161 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 87 408 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 87 - Jul 3 18:40:19 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 4 1034 Jul 3 18:40:19 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 4 6 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 88 253 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 88 - Jul 3 18:40:19 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 5 1030 Jul 3 18:40:19 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 5 6 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 89 253 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 89 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 6 701 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 6 136 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 90 383 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 90 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 7 61 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 7 6 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 91 253 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 91 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 8 40 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 8 45 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 92 292 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 92 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 9 66 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 9 99 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 93 346 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 93 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 10 86 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 10 41 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 94 288 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 94 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 11 46 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 11 46 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 95 293 192.168.215.13 Jul 3 18:40:20 rad-accept <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 95 - Jul 3 18:40:20 eap-success <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 11 4 Jul 3 18:40:20 wpa2-key1 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - 117 Jul 3 18:40:20 wpa2-key2 -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - 123 Jul 3 18:40:20 wpa2-key3 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - 191 Jul 3 18:40:20 wpa2-key4 -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - 95 AP505# show ap debug mgmt-frames Traced 802.11 Management Frames ------------------------------- Timestamp stype SA DA BSS signal Misc --------- ----- -- -- --- ------ ---- Jul 3 18:40:19.588 assoc-resp b8:3a:5a:8b:36:d0 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 15 Success Jul 3 18:40:19.588 assoc-req 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 b8:3a:5a:8b:36:d0 48 - Jul 3 18:40:19.585 auth b8:3a:5a:8b:36:d0 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 15 Success (seq num 0) Jul 3 18:40:19.585 auth 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 b8:3a:5a:8b:36:d0 0 -
- WPA2 対応の Galaxy SC-04F (MAC address = 90:b6:86:6b:e1:1f) 接続時
Auth Trace Buffer ----------------- Jul 3 18:40:39 station-up * 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - - wpa2 aes Jul 3 18:40:39 eap-id-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 1 5 Jul 3 18:40:39 eap-id-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 1 10 user2 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 96 215 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 96 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 2 6 Jul 3 18:40:39 eap-nak -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 2 6 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 97 253 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 97 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 3 6 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 3 164 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 98 411 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 98 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 4 1034 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 4 6 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 99 253 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 99 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 5 1030 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 5 6 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 100 253 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 100 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 6 701 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 6 132 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 101 379 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 101 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 7 61 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 7 6 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 102 253 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 102 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 8 40 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 8 45 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 103 292 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 103 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 9 66 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 9 99 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 104 346 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 104 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 10 86 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 10 41 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 105 288 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 105 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 11 46 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 11 46 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 106 293 192.168.215.13 Jul 3 18:40:39 rad-accept <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 106 - Jul 3 18:40:39 eap-success <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 11 4 Jul 3 18:40:39 wpa2-key1 <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - 117 Jul 3 18:40:39 wpa2-key2 -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - 123 Jul 3 18:40:39 wpa2-key3 <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - 191 Jul 3 18:40:40 wpa2-key4 -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - 95 AP505# show ap debug mgmt-frames Traced 802.11 Management Frames ------------------------------- Timestamp stype SA DA BSS signal Misc --------- ----- -- -- --- ------ ---- Jul 3 18:40:39.402 assoc-resp b8:3a:5a:8b:36:d0 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 15 Success Jul 3 18:40:39.402 assoc-req 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 b8:3a:5a:8b:36:d0 56 - Jul 3 18:40:39.400 auth b8:3a:5a:8b:36:d0 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 15 Success (seq num 0) Jul 3 18:40:39.400 auth 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 b8:3a:5a:8b:36:d0 0 -
- Association 情報
iPhone SE および Galaxy ともに、w: 802.11w client フラグ、E: Enterprise client フラグが付いていることが分かるが、WPA3 対応かどうかの判断はできなかった。
AP505# show ap association
The phy column shows client's operational capabilities for current association
Flags: H: Hotspot(802.11u) client, K: 802.11K client, M: VHT Mu beam formee, R: 802.11R client, W: WMM client, w: 802.11w client, V: 802.11v BSS trans capable, P: Punctured preamble, U: HE UL Mu-mimo, O: OWE client, S: SAE client, E: Enterprise client, m: Agile Multiband client, C: Cellular Data Capable - network available, c: Cellular Data Capable - network unavailable, T: Individual TWT client, t: Broadcast TWT client
PHY Details: HT : High throughput; 20: 20MHz; 40: 40MHz; t: turbo-rates (256-QAM)
VHT : Very High throughput; 80: 80MHz; 160: 160MHz; 80p80: 80MHz + 80MHz
HE : High Efficiency; 80: 80MHz; 160: 160MHz; 80p80: 80MHz + 80MHz
<n>ss: <n> spatial streams
Association Table
-----------------
Name bssid mac auth assoc aid l-int essid vlan-id phy assoc. time num assoc Flags DataReady UAC
---- ----- --- ---- ----- --- ----- ----- ------- --- ----------- --------- ----- --------- ---
AP505 b8:3a:5a:8b:36:d0 84:ab:1a:11:d2:f6 y y 1 20 bin4-wpa3-enterprise-ccm128 1 a-HE-20-2ss 55s 1 WVwE Yes (Implicit) 0.0.0.0
AP505 b8:3a:5a:8b:36:d0 90:b6:86:6b:e1:1f y y 2 10 bin4-wpa3-enterprise-ccm128 1 a-VHT-20sgi-2ss 35s 1 WVwE Yes (Implicit) 0.0.0.0
Num Clients:2
- Client-table 情報
e - Beamformer フラグがついているが、こちらからは特に違いがなかった。
AP505# show ap debug client-table
Client Table
------------
MAC ESSID BSSID Assoc_State HT_State AID PS_State UAPSD TWT Tx_Pkts Rx_Pkts PS_Qlen Tx_Retries Tx_Rate Rx_Rate Last_ACK_SNR Last_Rx_SNR TX_Chains Tx_Timestamp Rx_Timestamp MFP Status (C,R) Idle time Client health (C/R) Tx_Bytes Rx_Bytes
--- ----- ----- ----------- -------- --- -------- ----- --- ------- ------- ------- ---------- ------- ------- ------------ ----------- --------- ------------ ------------ ---------------- --------- ------------------- -------- --------
90:b6:86:6b:e1:1f bin4-wpa3-enterprise-ccm128 b8:3a:5a:8b:36:d0 Associated AWvSsEe 0x2 Power-save (0,0,0,0,N/A,0) (0,0) 71 263 0 0 173 173 60 60 2[0x3] Fri Jul 3 18:41:07 2020 Fri Jul 3 18:41:14 2020 (1,1) 0 100/27 38062 11189
84:ab:1a:11:d2:f6 bin4-wpa3-enterprise-ccm128 b8:3a:5a:8b:36:d0 Associated AWvSsE 0x1 Awake (0,0,0,0,N/A,0) (0,0) 242 432 0 0 270 286 50 48 2[0x3] Fri Jul 3 18:41:14 2020 Fri Jul 3 18:41:14 2020 (1,1) 0 100/27 232574 24767
Num of associated clients: 2
UAPSD:(VO,VI,BK,BE,Max SP,Q Len)
TWT:(iTWT sessions num, bTWT groups num)
HT Flags: A - LDPC Coding; B - TX STBC; D - Delayed BA; G - Greenfield
I - HT40 Intolerant; M - Max A-MSDU; N - A-MPDU disabled
Q - Static SM PS; R - Dynamic SM PS; S - Short GI 40; W - 40 MHz
b - RX STBC; s - Short GI 20; t - turbo-rates (256-QAM)
VHT Flags: C - 160MHz/80+80MHz; E - Beamformee; V - Short GI 160
c - 80MHz; e - Beamformer; v - Short GI 80
HT_State shows client's original capabilities (not operational capabilities)
MFP Status: C - 1 if the station is MFP capable; R - 1 if the station has negotiated MFP
- WPA3 対応の iPhone SE 接続時の無線キャプチャ
WPA3 対応端末と WPA2 対応端末でシーケンスに違いを見つけられませんでした。

- WPA2 対応の Galaxy 接続時の無線キャプチャ

[English Version]
I tried to connect iPhone SE/iOS13.5.1 which supports WPA3 and Galaxy SC-04F/Android 6.0.1 which support WPA2 to Aruba AP505/Instant OS 8.7.0.0 WPA3-Enterprise CCM128 (SSID: bin4-wpa3-enterprise-ccm128) with EAP-PEAP. In WPA3-Enterprise CCM128, 802.11w PMFC (Management Frame Protection Capable) is enabled, but almost same as WPA2-Enterprise, hence WPA2 device can associate. Like WPA3-Personal, we do not need to set opmode-transition option.
AP505# show ap debug auth-trace-buf Auth Trace Buffer ----------------- Jul 3 18:40:19 station-up * 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - - wpa2 aes Jul 3 18:40:19 eap-id-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 1 5 Jul 3 18:40:19 eap-id-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 1 10 user1 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 85 215 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 85 - Jul 3 18:40:19 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 2 6 Jul 3 18:40:19 eap-nak -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 2 8 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 86 255 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 86 - Jul 3 18:40:19 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 3 6 Jul 3 18:40:19 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 3 161 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 87 408 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 87 - Jul 3 18:40:19 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 4 1034 Jul 3 18:40:19 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 4 6 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 88 253 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 88 - Jul 3 18:40:19 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 5 1030 Jul 3 18:40:19 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 5 6 Jul 3 18:40:19 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 89 253 192.168.215.13 Jul 3 18:40:19 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 89 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 6 701 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 6 136 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 90 383 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 90 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 7 61 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 7 6 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 91 253 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 91 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 8 40 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 8 45 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 92 292 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 92 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 9 66 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 9 99 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 93 346 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 93 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 10 86 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 10 41 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 94 288 192.168.215.13 Jul 3 18:40:20 rad-resp <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 94 - Jul 3 18:40:20 eap-req <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 11 46 Jul 3 18:40:20 eap-resp -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 11 46 Jul 3 18:40:20 rad-req -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 95 293 192.168.215.13 Jul 3 18:40:20 rad-accept <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0/clearpass 95 - Jul 3 18:40:20 eap-success <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 11 4 Jul 3 18:40:20 wpa2-key1 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - 117 Jul 3 18:40:20 wpa2-key2 -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - 123 Jul 3 18:40:20 wpa2-key3 <- 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - 191 Jul 3 18:40:20 wpa2-key4 -> 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 - 95 AP505# show ap debug mgmt-frames Traced 802.11 Management Frames ------------------------------- Timestamp stype SA DA BSS signal Misc --------- ----- -- -- --- ------ ---- Jul 3 18:40:19.588 assoc-resp b8:3a:5a:8b:36:d0 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 15 Success Jul 3 18:40:19.588 assoc-req 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 b8:3a:5a:8b:36:d0 48 - Jul 3 18:40:19.585 auth b8:3a:5a:8b:36:d0 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 15 Success (seq num 0) Jul 3 18:40:19.585 auth 84:ab:1a:11:d2:f6 b8:3a:5a:8b:36:d0 b8:3a:5a:8b:36:d0 0 -
- Connecting Galaxy SC-04F (MAC address = 90:b6:86:6b:e1:1f)
Auth Trace Buffer ----------------- Jul 3 18:40:39 station-up * 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - - wpa2 aes Jul 3 18:40:39 eap-id-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 1 5 Jul 3 18:40:39 eap-id-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 1 10 user2 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 96 215 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 96 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 2 6 Jul 3 18:40:39 eap-nak -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 2 6 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 97 253 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 97 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 3 6 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 3 164 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 98 411 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 98 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 4 1034 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 4 6 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 99 253 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 99 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 5 1030 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 5 6 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 100 253 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 100 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 6 701 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 6 132 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 101 379 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 101 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 7 61 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 7 6 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 102 253 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 102 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 8 40 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 8 45 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 103 292 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 103 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 9 66 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 9 99 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 104 346 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 104 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 10 86 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 10 41 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 105 288 192.168.215.13 Jul 3 18:40:39 rad-resp <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 105 - Jul 3 18:40:39 eap-req <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 11 46 Jul 3 18:40:39 eap-resp -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 11 46 Jul 3 18:40:39 rad-req -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 106 293 192.168.215.13 Jul 3 18:40:39 rad-accept <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0/clearpass 106 - Jul 3 18:40:39 eap-success <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 11 4 Jul 3 18:40:39 wpa2-key1 <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - 117 Jul 3 18:40:39 wpa2-key2 -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - 123 Jul 3 18:40:39 wpa2-key3 <- 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - 191 Jul 3 18:40:40 wpa2-key4 -> 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 - 95 AP505# show ap debug mgmt-frames Traced 802.11 Management Frames ------------------------------- Timestamp stype SA DA BSS signal Misc --------- ----- -- -- --- ------ ---- Jul 3 18:40:39.402 assoc-resp b8:3a:5a:8b:36:d0 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 15 Success Jul 3 18:40:39.402 assoc-req 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 b8:3a:5a:8b:36:d0 56 - Jul 3 18:40:39.400 auth b8:3a:5a:8b:36:d0 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 15 Success (seq num 0) Jul 3 18:40:39.400 auth 90:b6:86:6b:e1:1f b8:3a:5a:8b:36:d0 b8:3a:5a:8b:36:d0 0 -
- Association information
We can see w: 802.11w client flag and E: Enterprise client flag on both devices, but we can not recognize WPA3 enabled or not.
AP505# show ap association
The phy column shows client's operational capabilities for current association
Flags: H: Hotspot(802.11u) client, K: 802.11K client, M: VHT Mu beam formee, R: 802.11R client, W: WMM client, w: 802.11w client, V: 802.11v BSS trans capable, P: Punctured preamble, U: HE UL Mu-mimo, O: OWE client, S: SAE client, E: Enterprise client, m: Agile Multiband client, C: Cellular Data Capable - network available, c: Cellular Data Capable - network unavailable, T: Individual TWT client, t: Broadcast TWT client
PHY Details: HT : High throughput; 20: 20MHz; 40: 40MHz; t: turbo-rates (256-QAM)
VHT : Very High throughput; 80: 80MHz; 160: 160MHz; 80p80: 80MHz + 80MHz
HE : High Efficiency; 80: 80MHz; 160: 160MHz; 80p80: 80MHz + 80MHz
<n>ss: <n> spatial streams
Association Table
-----------------
Name bssid mac auth assoc aid l-int essid vlan-id phy assoc. time num assoc Flags DataReady UAC
---- ----- --- ---- ----- --- ----- ----- ------- --- ----------- --------- ----- --------- ---
AP505 b8:3a:5a:8b:36:d0 84:ab:1a:11:d2:f6 y y 1 20 bin4-wpa3-enterprise-ccm128 1 a-HE-20-2ss 55s 1 WVwE Yes (Implicit) 0.0.0.0
AP505 b8:3a:5a:8b:36:d0 90:b6:86:6b:e1:1f y y 2 10 bin4-wpa3-enterprise-ccm128 1 a-VHT-20sgi-2ss 35s 1 WVwE Yes (Implicit) 0.0.0.0
Num Clients:2
- Client-table information
There is e - Beamformer flag on iPhone SE, but we can not recognize WPA3 enabled or not.
AP505# show ap debug client-table
Client Table
------------
MAC ESSID BSSID Assoc_State HT_State AID PS_State UAPSD TWT Tx_Pkts Rx_Pkts PS_Qlen Tx_Retries Tx_Rate Rx_Rate Last_ACK_SNR Last_Rx_SNR TX_Chains Tx_Timestamp Rx_Timestamp MFP Status (C,R) Idle time Client health (C/R) Tx_Bytes Rx_Bytes
--- ----- ----- ----------- -------- --- -------- ----- --- ------- ------- ------- ---------- ------- ------- ------------ ----------- --------- ------------ ------------ ---------------- --------- ------------------- -------- --------
90:b6:86:6b:e1:1f bin4-wpa3-enterprise-ccm128 b8:3a:5a:8b:36:d0 Associated AWvSsEe 0x2 Power-save (0,0,0,0,N/A,0) (0,0) 71 263 0 0 173 173 60 60 2[0x3] Fri Jul 3 18:41:07 2020 Fri Jul 3 18:41:14 2020 (1,1) 0 100/27 38062 11189
84:ab:1a:11:d2:f6 bin4-wpa3-enterprise-ccm128 b8:3a:5a:8b:36:d0 Associated AWvSsE 0x1 Awake (0,0,0,0,N/A,0) (0,0) 242 432 0 0 270 286 50 48 2[0x3] Fri Jul 3 18:41:14 2020 Fri Jul 3 18:41:14 2020 (1,1) 0 100/27 232574 24767
Num of associated clients: 2
UAPSD:(VO,VI,BK,BE,Max SP,Q Len)
TWT:(iTWT sessions num, bTWT groups num)
HT Flags: A - LDPC Coding; B - TX STBC; D - Delayed BA; G - Greenfield
I - HT40 Intolerant; M - Max A-MSDU; N - A-MPDU disabled
Q - Static SM PS; R - Dynamic SM PS; S - Short GI 40; W - 40 MHz
b - RX STBC; s - Short GI 20; t - turbo-rates (256-QAM)
VHT Flags: C - 160MHz/80+80MHz; E - Beamformee; V - Short GI 160
c - 80MHz; e - Beamformer; v - Short GI 80
HT_State shows client's original capabilities (not operational capabilities)
MFP Status: C - 1 if the station is MFP capable; R - 1 if the station has negotiated MFP
As far as I checked, there is no difference between iPhone SE connection sequence and Galaxy one.

- air capture on connecting Galaxy

WPA3-Enterprise Beacon
アルバの WPA3-Enterprise には、CCM 128、GCM 256、CNSA の3つのモードがある。各モードの Beacon フレームをキャプチャしてみました。各 SSID は、「bin4-wpa3-enterprise-ccm128」「bin4-wpa3-enterprise-gcm256」「bin4-wpa3-enterprise-cnsa」です。また、比較のために、WPA2-Enterprise の Beacon フレーム(SSID 「bin4-wpa2-enterprise」)もキャプチャしてみました。
- show ap bss-table コマンド
AP505# show ap bss-table Aruba AP BSS Table ------------------ bss ess port ip phy type ch/EIRP/max-EIRP cur-cl ap name in-t(s) tot-t flags --- --- ---- -- --- ---- ---------------- ------ ------- ------- ----- ----- b8:3a:5a:8b:36:d0 bin4-wpa3-enterprise-ccm128 ?/? 192.168.215.13 a-HE ap 108/18.0/29.7 0 AP505 0 28m:21s W3T b8:3a:5a:8b:36:d1 bin4-wpa3-enterprise-gcm256 ?/? 192.168.215.13 a-HE ap 108/18.0/29.7 0 AP505 0 24m:12s W3T b8:3a:5a:8b:36:d2 bin4-wpa3-enterprise-cnsa ?/? 192.168.215.13 a-HE ap 108/18.0/29.7 0 AP505 0 23m:51s W3T b8:3a:5a:8b:36:d3 bin4-wpa2-enterprise ?/? 192.168.215.13 a-HE ap 108/18.0/29.7 0 AP505 0 23m:33s T Channel followed by "*" indicates channel selected due to unsupported configured channel. "Spectrum" followed by "^" indicates Local Spectrum Override in effect. Num APs:5 Num Associations:0 Flags: K = 802.11K Enabled; W = 802.11W Enabled; r = 802.11r Enabled; 3 = WPA3 BSS; O = Enhanced-open BSS with transition mode; o = Enhanced-open transition mode open BSS; M = WPA3-SAE mixed mode BSS; E = Enhanced-open BSS without transition mode; m = Agile Multiband (MBO) BSS; c = MBO Cellular Data Capable BSS; I = Imminent VAP Down; T = Individual TWT Enabled; t = Broadcast TWT Enabled; d = Deferred Delete Pending; a = Airslice policy; A = Airslice app monitoring; D = VLAN Discovered; AP505#
- bin4-wpa3-enterprise-ccm128 の Beacon フレーム

RSN Information タグの AKM (Auth Key Management) が 00:0f:ac:01 (WPA) 、各暗号スイートが CCM となっていることが確認できます。また、RSN Capabilities 内の 802.11w/PMF (Protected Management Frames) が PMFR=0、PMFC=1 となっていることが確認できます。
- bin4-wpa3-enterprise-gcm256 の Beacon フレーム

RSN Information タグの AKM (Auth Key Management) が 00:0f:ac:05 (WPA:SHA256) 、各暗号スイートが GCM256/SHA256 となっていることが確認できます。また、RSN Capabilities 内の 802.11w/PMF (Protected Management Frames) が PMFR=1、PMFC=1 となっていることが確認できます
- bin4-wpa3-enterprise-cnsa の Beacon フレーム

RSN Information タグの AKM (Auth Key Management) が 00:0f:ac:0c (WPA:SHA384-SuiteB) 、各暗号スイートが GCM256/SHA384 となっていることが確認できます。また、RSN Capabilities 内の 802.11w/PMF (Protected Management Frames) が PMFR=1、PMFC=1 となっていることが確認できます
- bin4-wpa2-enterprise の Beacon フレーム

RSN Information タグの AKM (Auth Key Management) が 00:0f:ac:01 (WPA) 、各暗号スイートが CCM となっていることが確認できます。また、RSN Capabilities 内の 802.11w/PMF (Protected Management Frames) が PMFR=0、PMFC=0 となっていることが確認できます。
[English Version]
In Aruba, there are 3 types in WPA3-Enterprise mode, CCM 128, GCM 256 and CNSA. I captured WPA3-Enterprise Beacon frames. Each SSID name is bin4-wpa3-enterprise-ccm128, bin4-wpa3-enterprise-gcm256 and bin4-wpa3-enterprise-cnsa. I also captured WPA2-Enterprise Beacon frames for comparison (SSID: bin4-wpa2-enterprise).

- output of show ap bss-table
AP505# show ap bss-table Aruba AP BSS Table ------------------ bss ess port ip phy type ch/EIRP/max-EIRP cur-cl ap name in-t(s) tot-t flags --- --- ---- -- --- ---- ---------------- ------ ------- ------- ----- ----- b8:3a:5a:8b:36:d0 bin4-wpa3-enterprise-ccm128 ?/? 192.168.215.13 a-HE ap 108/18.0/29.7 0 AP505 0 28m:21s W3T b8:3a:5a:8b:36:d1 bin4-wpa3-enterprise-gcm256 ?/? 192.168.215.13 a-HE ap 108/18.0/29.7 0 AP505 0 24m:12s W3T b8:3a:5a:8b:36:d2 bin4-wpa3-enterprise-cnsa ?/? 192.168.215.13 a-HE ap 108/18.0/29.7 0 AP505 0 23m:51s W3T b8:3a:5a:8b:36:d3 bin4-wpa2-enterprise ?/? 192.168.215.13 a-HE ap 108/18.0/29.7 0 AP505 0 23m:33s T Channel followed by "*" indicates channel selected due to unsupported configured channel. "Spectrum" followed by "^" indicates Local Spectrum Override in effect. Num APs:5 Num Associations:0 Flags: K = 802.11K Enabled; W = 802.11W Enabled; r = 802.11r Enabled; 3 = WPA3 BSS; O = Enhanced-open BSS with transition mode; o = Enhanced-open transition mode open BSS; M = WPA3-SAE mixed mode BSS; E = Enhanced-open BSS without transition mode; m = Agile Multiband (MBO) BSS; c = MBO Cellular Data Capable BSS; I = Imminent VAP Down; T = Individual TWT Enabled; t = Broadcast TWT Enabled; d = Deferred Delete Pending; a = Airslice policy; A = Airslice app monitoring; D = VLAN Discovered; AP505#
- bin4-wpa3-enterprise-ccm128 Beacon frame

In RSN Information Tag, there are AKM (Auth Key Management) 00:0f:ac:01 (WPA) and cipher suite is CCM. In RSN Capabilities, we can see PMFR=0 and PMFC=1 of 802.11w/PMF (Protected Management Frames).
- bin4-wpa3-enterprise-gcm256 Beacon frame

In RSN Information Tag, there are AKM (Auth Key Management) 00:0f:ac:05 (WPA:SHA256) and cipher suite is GCM256/SHA256. In RSN Capabilities, we can see PMFR=1 and PMFC=1 of 802.11w/PMF (Protected Management Frames).
- bin4-wpa3-enterprise-cnsa Beacon frame

In RSN Information Tag, there are AKM (Auth Key Management) 00:0f:ac:0c (WPA:SHA384-SuiteB) and cipher suite is GCM256/SHA384. In RSN Capabilities, we can see PMFR=1 and PMFC=1 of 802.11w/PMF (Protected Management Frames).
- bin4-wpa2-enterprise Beacon frame

In RSN Information Tag, there are AKM (Auth Key Management) 00:0f:ac:01 (WPA) and cipher suite is CCM. In RSN Capabilities, we can see PMFR=0 and PMFC=0 of 802.11w/PMF (Protected Management Frames).
WPA2-Personal PSK passphrase mismatch
比較として、WPA2-Personal PSKパスフレーズを間違えて入力した場合のログを見てみましょう。
Auth、Assoc、4-way handshake を実施していないことが分かりますが、4-way handshake の Key2 で mic failure となっていることがわかります。WPA3 の場合と、だいぶ違いますね。
AP505# show ap debug auth-trace-buf Auth Trace Buffer ----------------- Jul 1 11:50:06 station-up * 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - - wpa2 psk aes Jul 1 11:50:06 wpa2-key1 <- 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 Jul 1 11:50:06 wpa2-key2 -> 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 mic failure Jul 1 11:50:07 wpa2-key1 <- 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 Jul 1 11:50:07 wpa2-key2 -> 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 mic failure Jul 1 11:50:08 wpa2-key1 <- 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 Jul 1 11:50:09 wpa2-key2 -> 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 mic failure Jul 1 11:50:10 wpa2-key1 <- 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 Jul 1 11:50:10 wpa2-key2 -> 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 mic failure AP505# show ap debug mgmt-frames Traced 802.11 Management Frames ------------------------------- Timestamp stype SA DA BSS signal Misc --------- ----- -- -- --- ------ ---- Jul 1 11:50:06.099 assoc-resp b8:3a:5a:8b:36:d1 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 15 Success Jul 1 11:50:06.099 assoc-req 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 b8:3a:5a:8b:36:d1 43 - Jul 1 11:50:06.097 auth b8:3a:5a:8b:36:d1 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 15 Success (seq num 0) Jul 1 11:50:06.097 auth 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 b8:3a:5a:8b:36:d1 0 -
また、show log security コマンドにて、4-way handshake の Key2 で MIC Failed が発生しているログが確認できます。
AP505# show log security Jul 1 11:50:06 stm[5309]: <132094> <WARN> |AP AP505@192.168.210.215 stm| MIC failed in WPA2 Key Message 2 from Station 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 AP505
[English Version]
For comparison, let's see when WPA2-Personal PSK passphrase mismatch happens.
We can see Auth, Assoc and 4-way handshake, but we can see mic failure in 4-way handshake Key2. There are a lot of difference from WPA3-Personal PSK passphrase mismatch.
AP505# show ap debug auth-trace-buf Auth Trace Buffer ----------------- Jul 1 11:50:06 station-up * 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - - wpa2 psk aes Jul 1 11:50:06 wpa2-key1 <- 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 Jul 1 11:50:06 wpa2-key2 -> 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 mic failure Jul 1 11:50:07 wpa2-key1 <- 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 Jul 1 11:50:07 wpa2-key2 -> 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 mic failure Jul 1 11:50:08 wpa2-key1 <- 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 Jul 1 11:50:09 wpa2-key2 -> 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 mic failure Jul 1 11:50:10 wpa2-key1 <- 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 Jul 1 11:50:10 wpa2-key2 -> 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 - 117 mic failure AP505# show ap debug mgmt-frames Traced 802.11 Management Frames ------------------------------- Timestamp stype SA DA BSS signal Misc --------- ----- -- -- --- ------ ---- Jul 1 11:50:06.099 assoc-resp b8:3a:5a:8b:36:d1 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 15 Success Jul 1 11:50:06.099 assoc-req 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 b8:3a:5a:8b:36:d1 43 - Jul 1 11:50:06.097 auth b8:3a:5a:8b:36:d1 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 15 Success (seq num 0) Jul 1 11:50:06.097 auth 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 b8:3a:5a:8b:36:d1 0 -
From show log security, we can see MIC Failed log in 4-way handshake Key2.
AP505# show log security Jul 1 11:50:06 stm[5309]: <132094> <WARN> |AP AP505@192.168.210.215 stm| MIC failed in WPA2 Key Message 2 from Station 04:69:f8:0c:88:a6 b8:3a:5a:8b:36:d1 AP505